One of the advantages of the blockchain technology is supposed to be the added security and resilience to cyber attacks. The open-source nature of blockchains does make them an open target for different types of attacks though. We explore three popular attacks and how to prevent them.
Examples of attacks to blockchains range from traditional and general threats that all network platforms face, to unique and specific attacks to blockchains. Before we go into depth about the types of attacks, we identify 4 elements of a blockchain which can face vulnerabilities:
- Blockchain nodes
- Smart contracts
- Consensus mechanisms
- Wallets
Distributed Denial of Service (DDoS)
A Distributed Denial of Service (DDoS) takes place when a malicious user floods a server or network with requests and traffic. A DDoS attack intends to slow down or collapse a system. Any form of the online platform can be vulnerable to DDoS attacks including company websites and servers.
Specifically, within a blockchain, a DDoS attack can overload a blockchain with incoming bits of data which can force a blockchain to sever to further utilize its processing power. Through doing this, a blockchain server can lose connectivity to any crypto exchanges, online crypto wallets, or any other connected applications.
There are several high profile cases of attackers utilizing DDoS principals to gain access to crypto exchanges. Between November and December 2017, popular exchange Bitfinex had been successfully DDoS attacked 3 times where attackers shut down the exchange. In both blockchain and non-blockchain focussed DDoS attacks, the overload of requests comes from either an individual or a small number of unique locations (which can be tracked through IP addresses).
How to prevent a DDoS attack on a blockchain?
Typically DDoS attacks are made possible through centralized features of a network such as a single point of connectivity to the internet. As a public blockchain is already a decentralized system linked to multiple nodes, a DDoS attack needs access to different nodes at the same time to inflict significant damage to the network.
The action of doing this makes the DDoS attack much more complex to pursue as well as considerably more time consuming compared to other methods of blockchain attacks. In 2016 the Ethereum Blockchain became a victim of a DDoS attack which considerably increased the time it took in creating and verifying blocks. In response, the Ethereum development team made changes to their miner software in which gas limit targets were reduced if the network experienced a similar attack where the creation of new blocks was taking a longer amount of time.
DDoS attacks are prevented through further decentralisation of a network. Not only would this reduce the capacity of a DDoS attack but also offer bandwidth to other specific servers facing attacks without compromising the whole chain. Even if certain nodes are compromised, taken offline, or disrupted, the blockchain can still operate and validate transactions. The disrupted nodes can recover and re-sync with unaffected nodes.
51% Attack
As referenced earlier in this article, a crucial feature of what makes a blockchain secure, lies within the decentralization and the ability of nodes to reach consensus. For example, the Proof of Work algorithm which is used by the Bitcoin blockchain forces all participants of the network to follow the same rules and protocols when miners are introducing new blocks, verified by nodes.
The decentralized element of blockchain ensures there is no individual or centralized entity from influencing the activities of the blockchain outside of the PoW consensus.
In a typical Blockchain network, new coins/tokens are unlocked through computers/miners that compete against each other in finding nonces that fit hashing problems. Once a miner successfully inputs the correct hashing combination and it is verified by the nodes and propagated throughout the network.
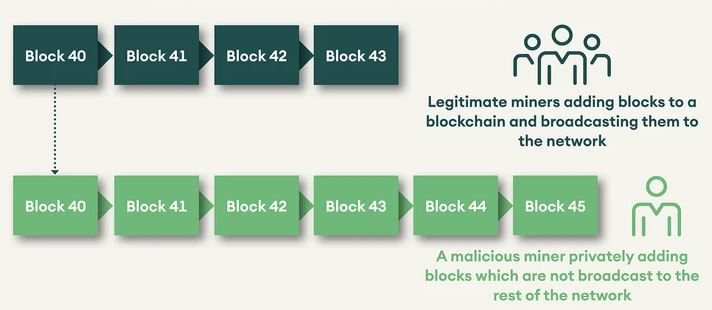
Figure 1: A demonstration of a 51% attack on a blockchain
A 51% attack takes place where a malicious individual or a group takes control of over 50% of a blockchain network hash rate. In having control of 51% of the hash rate, attackers can influence other blocks that hold their transactions. Figure 1 demonstrates how a 51% attack takes place. Let’s say that the attacker has their transactions in the legitimate chain wherein they send transactions to exchanges, merchants etc. based on which they receive services.
For example, assume that block 40 has a transaction of token A sent to an exchange and as soon as the deposit is confirmed, the attacker converts token A to say ETH. Meanwhile, the attacker is mining blocks with their hashpower. In the private chain, the attacker sends the same transaction in block 40 to themselves instead of the exchange. As the attacker’s chain is longer (implying more work done), the network has to accept the new chain. In the new chain, token A never went to the exchange. Thus, the attacker has token A as well as ETH. The farther back the attacker goes in the chain, the higher is the damage. And the number of blocks that can be re-written by the attacker depends on the hashpower they have compared to the network.
Key incentives for attackers to conduct 51% attacks include the possibility of “double spending”. Double spending takes place where a malicious entity controls more than 51% of the hashing power and can create a copy of a transaction and add it to a blockchain. This erases earlier transactions on the network as if they never took place.
This, in turn, means attackers can spend their tokens multiple times through erasing other blocks.
Over the past few years, there have been a few 51% attacks. In the past 3 months, attackers have been able to fraudulently steal over USD 8 million worth of ETC. The latest Ethereum Classic 51% attack in which attackers were able to ‘reorganize’ over 7000 blocks. This was the third 51% attack the blockchain had faced in recent times and the ETC blockchain is now trialling a strategy to stabilize the networks decreasing hash rate to avoid future attacks. Other major attacks include:
- Ethereum Classic 51% attack in 2019 causing a loss of $1.1m
- Verge 51% attack in 2018 causing a loss of $1.75m.
- Verge was later attacked (51% attack) 2018 resulting in a loss of $1.1m
In Jan 2020, the Bitcoin Gold blockchain was the target of a 51% hack which resulted in attackers double-spending over $85,000 worth of Bitcoin Gold. Some people speculated that attackers were able to obtain mining power through the online mining power market place “NiceHash”. Currently, NiceHash allows users to rent mining power for over 33 major blockchain algorithms.
Blockchains that use a PoW consensus algorithm are vulnerable to 51% attacks because the network is open for anyone to mine, including attackers. The lower the hash rate the blockchain the easier it is for an attacker to gain a majority advantage. Popular blockchains such as Bitcoin or Ethereum (both run PoW) have a very low vulnerability risk to 51% attack as gaining 50% of their networks would require an unrealistic amount of computational and energy resources.
How to prevent a 51% attack?
Blockchains that use a PoW consensus algorithm are vulnerable to 51% attacks because the network is open for anyone to mine, including attackers. The lower the hash rate the blockchain the easier it is for an attacker to gain a majority advantage. Popular blockchains such as Bitcoin or Ethereum (both run PoW) have a very low vulnerability risk to 51% attack as gaining 50% of their networks would require an unrealistic amount of computational and energy resources. In sum, the higher the hashrate, the more difficult it is to perform a 51% attack.
Sybil Attacks
Sybil Attacks manipulate online systems where one user attempts to overpower a network through the use of multiple profiles. Specifically, with blockchains, Sybil Attacks are when a user attempts to run multiple nodes on a blockchain network.
Figure 2: Illustration of a Sybil Attack, connecting to a Node and masking uncorrupted nodes.
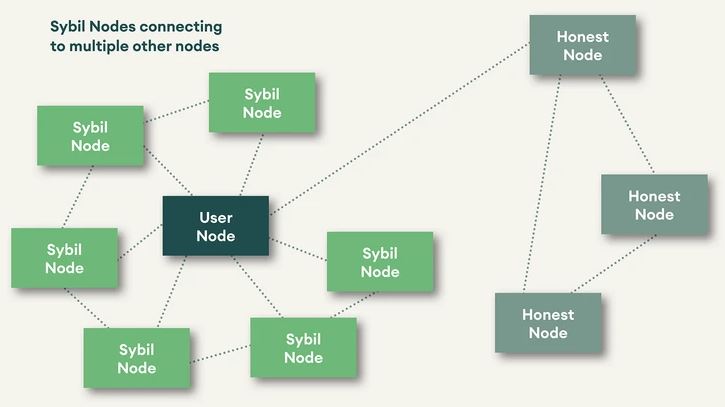
A successful Sybil attack on a blockchain can force a network into influencing other nodes (if they can create enough nodes). Through controlling nodes, the Sybil attackers can refuse to transmit blocks which effectively prevents users from adding data to the network.
It is important to add that Sybil attacks can lead to a malicious user (or users) to control the majority of a blockchain network. In doing this they can conduct a 51% attack where they could manipulate transactions and even force to double spend.
How to prevent a Sybil Attack?
Though consensus algorithms do not prevent Sybil attacks, they make it difficult and impractical for the attacker to carry out such an attack. For example, running full mining nodes on bitcoin network demands the attacker to possess significant hashpower which means the cost of an attack is high, and the expected rewards of a Sybil attack may not compensate for this cost. Therefore, it is in the best interest of an attacker to keep mining honestly.
Outside of PoW and PoS consensus algorithms, blockchains can prevent Sybil attacks through direct validation and indirect validation of new and existing members. Direct validation would allow existing members of a blockchain to verify new members joining a network, whereas indirect validation would allow existing members of a blockchain to provide authorisation rights to other members.
Conclusion
In this article, we have highlighted three well-known attacks and we might discuss less common but highly impactful attacks in future articles. With the rising popularity of platforms such as NiceHash, attackers can rent mining power to conduct attacks such as the 51% attack with much less mining power and mining expertise of their own. The permissionless and censorship-resistant nature of public blockchains also means that the attack surfaces are larger. Blockchains such as Bitcoin and Ethereum are becoming increasingly difficult to attack while vulnerabilities in the smaller blockchains will get exploited further.