Basically, any application that includes functions for storing and handling cryptocurrencies can be called a crypto wallet. A detailed introduction to how wallets work and an overview of different types of crypto wallets and their use cases.
It is important to note that cryptocurrencies are not stored on the wallet itself, but on the blockchain. The coins/token on the blockchain are assigned to a publicly visible address. These addresses can be viewed with block explorers. Apart from privacy coin logs, transaction histories and balances of addresses are publicly accessible.
The public address is generated from the private key by a complex mathematical algorithm. It is almost impossible to reverse the process by generating a private key from a public key. Only the owner of the private key has access to the coins.
Software to access crypto wallets
There are crypto wallets that can only manage the coins of a specific cryptocurrency and there are wallets that can control multiple crypto assets (multicoin wallet). A wallet stores the users private key. When a transaction is initiated, the wallet software creates a digital signature by processing the transaction with the private key. This ensures a secure system, since the only way to generate a valid signature for a particular transaction is to use the private key.
While the private key guarantees access to an individual addresses, wallets often contain a seed phrase. The seed can be used to reinstall wallet software and restore the private keys and associated addresses. Note that the public address can be shared. The public address is the address with which you can receive crypto-currencies (comparable to a mailbox address). Private keys and seeds, on the other hand, must never be publicly available. With them you have access to the cryptocurrencies (keys to the mailbox). If private keys and seeds are lost, the cryptocurrencies are also lost.
A rule of thumb is: The easier it is to set up a crypto wallet, the less control you have over it. There are basically two types of wallets: in one case you are the owner of the private keys, in the other you are not (less secure). A distinction is also made between different types of wallet. Below is an overview, starting with the simplest variant.
Online Wallet
The term “online wallets” generally refers to web wallets and other services that can be accessed via a browser. Additionally, crypto assets which are held via trading platforms fall into this category. Storing excessive amounts on online wallets or at centralized exchanges should generally be avoided, as they bear the risk of falling victim to a computer hack. In the past, there have been a number of prominent cases where services have been hacked or the operators themselves have stolen the crypto assets. This behavior is only possible because you do not have your own private keys.
Web wallets offer the possibility to control coins and tokens online. These were particularly popular in the early days of the crypto era, as secure solutions were still very complex to use at that time. In the meantime, pure web wallets are a taboo and should no longer be used, since it is never certain who has access to the crypto assets and who is behind the services.
Although trading platforms or even exchanges are usually considered relatively secure, as they are often backed by a company with corresponding reputation risks, there are risks there too. In addition to hacks, which have also affected prominent exchanges in the past, access to personal accounts can also be blocked. This can be due to new compliance regulations introduced by the exchange, or it can simply happen by mistake. Bankruptcy of the trading platform cannot be ruled out either. In this case, it remains open how much of the remaining crypto-values would flow back to the users.
Classic problems like phishing and other hacker attacks are also a danger. Two-factor authentication should be used for the login. Exchanges should therefore only have short-term capital available, which has to be available for trading.
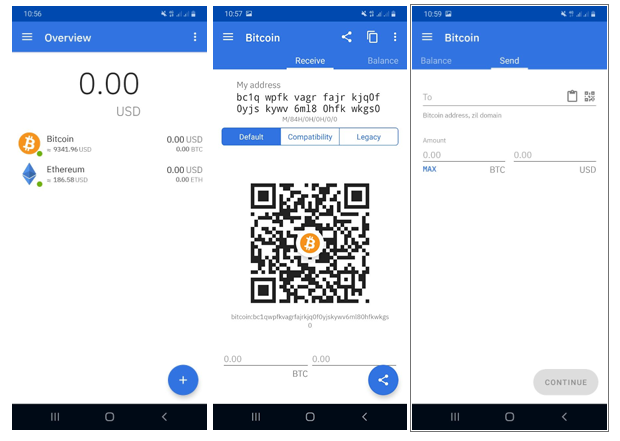
Mobile Wallet
With mobile wallets you can check your crypto assets on a smartphone or tablet. After downloading a mobile wallet app, an account is often created to access the coins. An advantage of mobile wallets is the possibility to scan QR codes which can be read with the camera of the smartphone. This is advantageous for payments, because in contrast to manual entry or copying the destination address, very little errors can occur. Also, the transaction costs to be paid are already included in the amount to ensure processing on the blockchain.
Mobile wallets also have similar risks like the exchanges. On the one hand there is a dependence on the manufacturer, on the other hand hacks are potentially possible. There are apps that work with a login and apps that store the wallet data locally on the device. This way you usually have control over the private keys or the seed. It is best to treat it like a wallet with cash. You only keep as many crypto assets in the wallet as you actually want to spend in the near future. Well-known examples are the BRD Wallet or Coinomi Wallet.
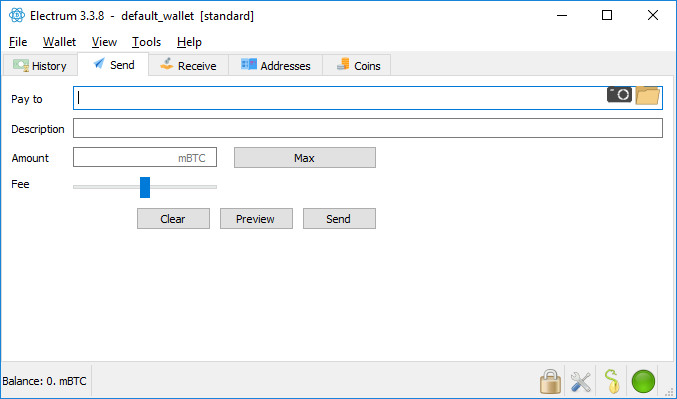
Desktop Wallet
Each public blockchain protocol of a cryptocurrency usually provides a desktop wallet to the users. Without this software, it is not possible to transfer the coins and integrate them into services such as exchanges. The situation is different for tokens, since they operate on an external platform (for example, Ethereum). In this case a wallet of the underlying platform is sufficient.
Desktop Wallets are available in different forms. Classically, they come with a graphical user interface. Often used wallets are the Electrum Wallet (Bitcoin-based cryptocurrencies) or Metamask (Ethereum-based protocols). But there are also command line based versions, which take the approach to be minimalistic, to offer less attack surfaces for hackers. Here the danger of a hack is also present, so it is important to protect your computer. Since you control your private keys yourself, a backup of them should be created in any case. Desktop wallets should not be used by private individuals for storing large sums of money as long as they are not used in combination with a hardware wallet.
Hardware Wallet
A hardware wallet is a device on which the private keys of crypto assets can be stored. In theory, this can be a simple USB stick, but this does not bring any additional functionality. Well-known hardware wallets like Trezor, Ledger and Bitbox offer different web interfaces to online services.
It should be noted that these devices do not support all crypto assets. And even more importantly, the so-called seed or recovery phrases must be stored securely in case the hardware wallet gets lost. Hardware wallets offer private users the highest security standard when used correctly.

Paper Wallet
A paper wallet is an offline mechanism for storing cryptocurrencies. In a paper wallet, the public address and private key are printed offline or written down on a sheet of paper. Also known as physical wallets, they are considered one of the most secure ways to store crypto assets if they are properly constructed and if certain precautions are taken.
Paper wallets can be generated using an open source wallet generator. It is generally recommended that users disconnect their internet access while the keys are being generated and that users delete their internet history after the keys are generated. Ideally, the keys should be created on a brand new computer to completely avoid malware interference.
Finally, the paper wallet is stored in a secure location such as a bank vault. Here, the physical piece of paper must be protected from damage. If the keys fade and can no longer be read, the user will no longer be able to access the crypto values stored at this address.
General rules of thumb
- Online services are not suitable for the safekeeping of larger sums.
- A backup of the private key and the seed should always be made (storage of the backup outside the internet, for example on a USB stick).
- A provision should be made for the event of your own death, so that the crypto assets are not lost.
- Transfers of crypto assets should be done with the necessary caution. It is important to check wallet addresses before making a transaction. Transactions on the blockchain cannot be reversed!
Wallets for interacting with smart contracts
In the age of DeFi and NFTs, wallets are not only used to store and transfer crypto assets, but also as an application for interacting with various blockchain platforms that use smart contracts. Wallets can be viewed as a "browser" for the Web 3.0 in dealing with decentralized financial transactions.
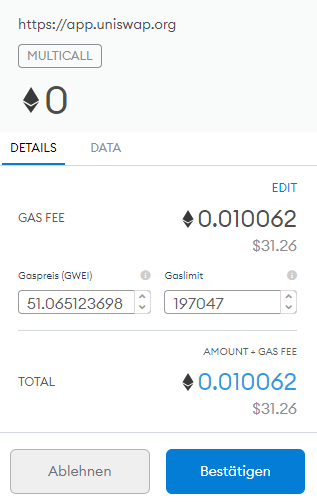 The wallet serves as an interface between the user and the smart contract platform. Through the wallet, the user allows a smart contract to perform a certain operation on the corresponding blockchain network.
The wallet serves as an interface between the user and the smart contract platform. Through the wallet, the user allows a smart contract to perform a certain operation on the corresponding blockchain network.
For example, if one wants to make an exchange from one cryptocurrency to another on a decentralized exchange, the wallet serves as an application to approve or execute the transaction.
In the illustrated example, the user allows an exchange to be completed on the decentralized trading platform via the wallet "Metamask,". Also visible are the network fees that are charged for this specific action.
Various DeFi applications and NFT marketplaces only work in cooperation with a wallet.